Protocols: Getting the most out of Covid19 incident management monitoring
Practitioners may be using crime/incident/protection/risk/investigation system be it a book, whiteboard or software to facilitate an incident management method.
Security success to limit the covid19 collateral damage will depend on the level of awareness of the people on the ground (all are decision-makers) and their reaction speed.
All Management can use the same system for distinct purpose.
- The Financial Department will use the information to manage their fast-changing budgeting for sick leave, cross-skilling, recruiting temporary staff, equipment and technology.
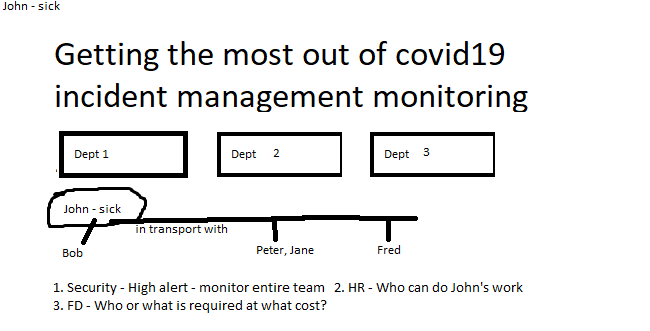
- The HR Department would advise information for the financial department and manage the manpower that would require the above besides, informing the security and investigation (sick-leave) on finding a person-of-interest and who they may be associating with, to build a list of people to be constantly monitored.
- The Security & Safety/Investigation Department would be able to support the finding of a person of concern using technology such as access control and cctv, probably with facial recognition and if necessary, temperature detection cctv or handheld devices. They in-turn could also inform the HR department on people of concern to HR.
- Knowledge of criminology would contribute towards the security department to identify possible new crimes, and copycat crime that could occur. For example; many people could become unemployed and resort to distinct increases in specific crime. Desperate people could do desperate things, or, people just go hysterically crazy!
The issues are is that the security, investigation, protection, safety and risk practitioners may need to quickly critical situational interview others using deception detection methods because they require above all – ‘all-the-truthful information’
It is vital to obtain all-the-truthful information because this is a life impacting and life & death incident.
The most important Tool that the practitioners could use is the HIM e-Connect Tool. Simply put, it contains protocols for specific sectors and guidance articles for many distinct fields of interest besides the easiest and most effective method to quickly acquire the methodology of reading people of concern to determine their linkage to others.
All protocols can be found on ISIO Intelligence Guidance Centre and HIM
All rights reserved
